I purposefully selected compartments and network segmentation as the example for this series, because I generally tend to see customers tend to confuse or correlate network design and compartment design and it generally tends to drag out the design process. When we are looking at compartment structure, we are looking at the segmentation and authorization requirements. So, it is not just network that needs to be considered in the IAM design, but rather a wholistic look at the segmentation requirements and how OCI policy can meet those segmentation requirements.
In this example, we are trying to come up with a compartment design that meets the following criteria:
- Create a compartment structure that will allow us to segment the software defined network access with IAM policy between projects or lines of business
- IAM policy does not provide a method to grant access to users at the subnet layer without using tag-based authentication
- Assuming we are not using tag-based authorization on the subnet’s, we will continue to look for the segmentation at the VCN and compartment levels which will allow us to provide segmentation with IAM policy
- Allow network admins to manage the software defined networks (sdn) within the tenancy
- We can assume the management is performed by one networking team, but we should keep in mind that there may be a requirement for network admins to be segmented by production or non-production, compartment, etc. in the future
In my previous post, we accomplished the segmentation by creating a top-level compartment for Network and then creating sub-compartments where the VCN’s would be defined. In that example, we can easily use IAM policy to grant management or use of the sdn at the sub-compartment level.
The top-level Network compartment design adds compartments to the overall design, with the number of sub-compartments required tied to segmentation required by VCN (i.e., for each segmented VCN, we will have a corresponding Network sub-compartment).
If customers do not like the idea of having a top-level Network compartment, another way to accomplish the segmentation is to deploy the networks within the project compartments. By deploying the VCN into the project compartments/sub-compartments, we can reduce the number of compartments defined in the tenancy. Reducing the number of compartments, can reduce operational overhead (which we discussed in part 1 of this series). One example of the reduced operational overhead would be the reduction in compartments reduces the the time and scope of tenancy scans as there are fewer compartments to traverse within the tenancy.
The alternative compartment structure could be as follows:
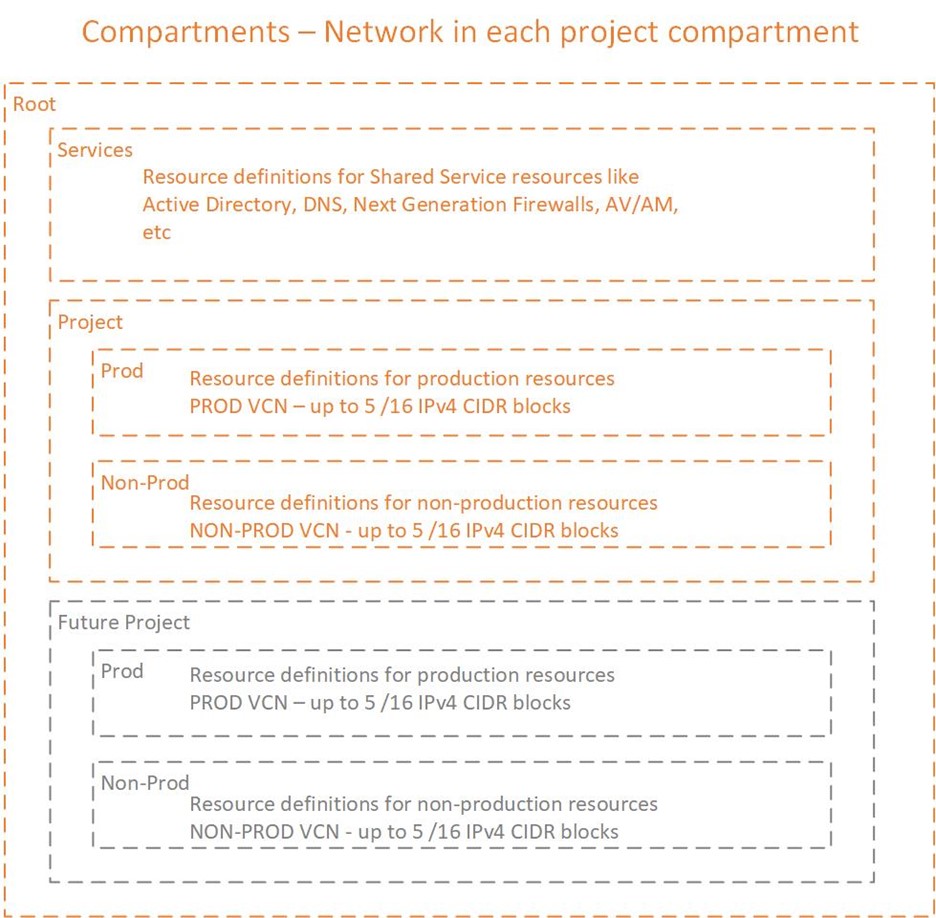
This design reduced the number of compartments, but what are some potential trade-offs?
- Network management overhead – Network admins still have the complexity to segment and track the CIDR ranges but with this design, the network admins will now need to navigate between the project compartments/sub-compartments to manage the networks. We can mitigate some of the added complexity with tagging, naming standards, etc. which will make it easy to find the network resources within the tenancy to reduce navigation and potential risk.
- Policies – In the previous design, we had the option to set the Network access at either the tenancy level, the Network compartment level or at the Network sub-compartment level. Applying policy to the top-level Network compartment applied to all of the sub-compartments. By moving the sdn into the project level compartment/sub-compartments we may have to set a network policy at each compartment. While we could simply have a policy to manage the network-family in the tenancy, I generally tend to see customers require a policy for the network admins per compartment/sub-compartment as they want the ability to easily apply segmentation in the future by prod vs non-prod (i.e., junior, and senior network admins having management access to non-prod and senior network admins to production network resources).
The differences between the two approaches are very subtle, but as I walk through design meetings with customers, I try to do the following:
- Ensure we have the proper stakeholders in the meeting/s (technical architects, security, network team representative)
- Technical architects will ensure the compartment pattern we are setting aligns with current design patterns and ensure we are designing in alignment with any future architecture considerationsSecurity team members will ensure that the design is meeting customer security standards for segmentation and policies that are not too generic
- Network team members will ensure that the design does not impose undo operational overhead for management of the networks
The last segment in this series explores how we can reduce compartments and the number of VCN by incorporating tag-based access controls.